
The IBM Onion of Security – it will make Hackers Cry!
Added Monday 12 August 2019 by Arrow
I can still recall the watershed moment it all fell into place …
It was halfway through the prestigious three day IBM Security Top Gun training, and we had already been bombarded by so many security product names and best practices that my head was swimming; I desperately needed to make sense of why there were so many products and how they all fitted together (particularly as there were tests ahead and the esteemed Top Gun cap to win ;-)
Sat at lunch, chatting to the other students, and toying with a slice of onion ring in my salad, I had my security epiphany! Protecting an enterprises’ business critical data and intellectual property (IP) was like an Onion of Security! The data and IP were at the heart of the onion, with hackers, criminals and other cyber-malcontents on the outside, trying to get through numerous layers of integrated and intelligent security.
So, what does the IBM Onion of Security look like and how does it work to protect business-critical assets? Here is my own personal take on this question …
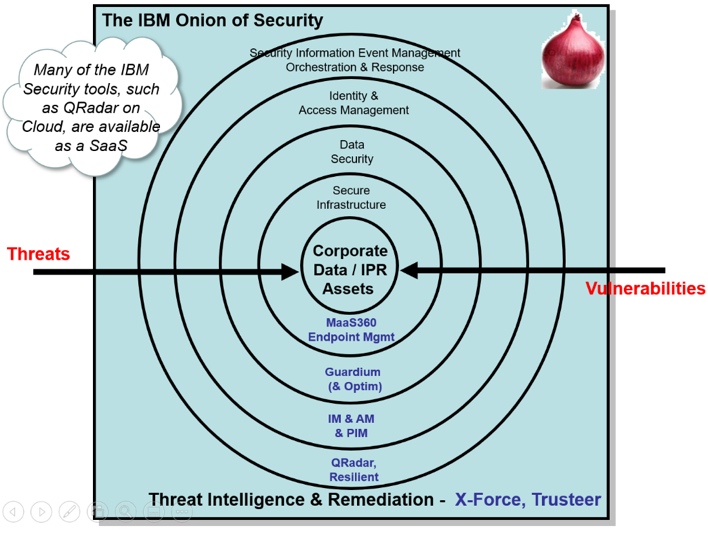
The IBM Onion of Security, is comprised of …
- The tough protective skin on the outside of the Onion provides the first contact with the outside world, monitoring and analysing any and all access to the inner layers, orchestrating the security of the Onion and its valuable core, and giving it its smarts (what? Can’t an onion be clever?). It is here that Security Information and Event Management (SIEM) is delivered by IBM QRadar, as well as supporting incident response through the Resilient
- The next layer, delivers effective and efficient Identity and Access Management delivering secure user authentication and authorization to applications and data. Security Identity Manager and Security Access Manager work as an integrated pair to provide single sign-on, user lifecycle management, automated user-ID and password management, and support your compliance needs with audit trail collection, analysis and reporting.
- The next layer, Infrastructure Security ensures that all parts of the Onion (and your diverse and complex IT estate) are identified and provided with the most up to date security protection, such as security patches and fixes, installed and working. IBM’s Rigorous endpoint management ensures that there are no vulnerabilities or holes in the security posture of all of the components within your IT estate; IBM MaaS360 performs end point management.
- The final layer of Data Security is delivered by Guardium, which acts like a protective shell that safeguards your data, monitoring who is accessing the information and for what purpose, and preventing and reporting any suspect activity. Guardium can also be used to encrypt your data (a typical compliance requirement), so that in the unlikely event that any data is accessed by an unauthorised 3rd party, it is useless to them.
- Lastly, the Onion sits in a safe nurturing environment, enjoying thorough Malware Protection through IBM Trusteer and being fed updates on the very latest IT security risks and venerability’s by the IBM X-Force team of elite ethical-hackers.
Hopefully, sharing my epiphany about the IBM Onion of Security has helped you understand what the IBM Security solutions can do for the customer and how they all fit together into an integrated and complete security solution.
In Part 2 of this Blog, I will explain in detail the tangible benefits the IBM security solutions can deliver.
More Information
If you’d like hear more about this, please complete the form below:
